Blog: Cyber security paramount for functioning of utility companies
Sharman Santosh
Recently a hacker managed to gain remote access to the operational system of a water recycling facility in Florida, USA. He illegally adjusted the values of the caustic soda solution to values that are potentially dangerous for drinking water. As a result, the discussion about the cyber security of drinking water facilities and other critical infrastructures flared up again.
The hacker of the Florida water recycling facility gained access to the plant through TeamViewer. This is standard software with which a user can log in to a system remotely and then operate it as if he were physically present to control the system. TeamViewer is often used by IT help desk employees to help colleagues solve their computer problems. Fortunately, at the affected Florida water recycling facility, an alert operator was able to prevent a disaster by intervening in time, but it shows that utilities are still too often vulnerable to cyberattacks.
Operational Technology
Just like energy companies, a water recycling facility is a critical infrastructure. To increase efficiency and enable remote access, such organizations make extensive use of ICT solutions. This so-called Operational Technology (OT) is innovating at a rapid pace. This ensures better performance and possibilities, but also entails risks. A serious threat such as that at the water recycling facility can also occur at other critical infrastructures, with serious consequences. In this case, it is important to consider how this incident could happen. But it is even more important to minimize the risk of cyber-attacks across the entire OT domain.
Processes and roles
Within the OT domain, digitisation has taken off perhaps most evidently in Industrial Automated Control Systems, also known as IACS. IACS comprises the entire system of people, hardware and software, processes, policy rules, etc. that must work together in a well-orchestrated manner to achieve the intended objectives. In order to guarantee security, in particular cyber security, within such a system and to prevent threats such as those at the Florida water recycling facility, it is important to check whether the various processes and associated roles are properly organised.
User accounts
For example, how did the management of the Florida water recycling facility deal with user account processes? These processes must have access to the correct information, so that each specific user can only perform actions in the water recycling facility for which he is authorized. So if you zoom in on the user accounts then they must contain the correct attributes, but also in the bigger picture authorization and privileges must be well arranged.
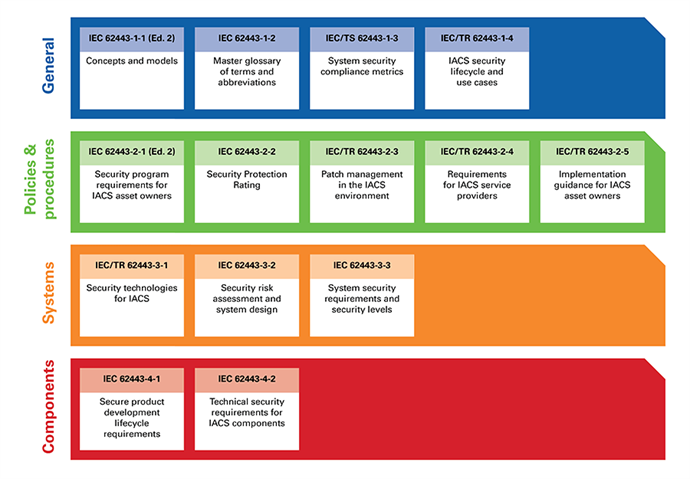
The IEC 62443 standard series
The IEC 62443 is a series of standards that ensures that cyber security within the OT domain, for example in critical infrastructure, is properly safeguarded. The standard consists of several sections and describes both technical and process-related aspects of industrial cybersecurity. The IEC 62443 (or ANSI/ISA 62443) standards framework distinguishes the target groups ‘End Users’ and ‘Solution Providers’. The term ‘Solution Providers’ refers to ‘Manufacturers’, ‘System Integrators’ and ‘Vendors’, but ultimately everyone is free to apply this standard. The breakdown of the standard looks like this:
- IEC 62443 1-X: General: General information about concepts, models and terminology. These standards lay the foundation upon which the other categories, such as ‘Policies & Procedures’, ‘System’ and ‘Components’ are based.
- IEC 62443 2-X: Policies & Procedures: This category indicates how policy measures must be structured so that cyber security can be dealt with in a structured manner. It is aimed at the ‘End Users’ and ‘Solution Providers’ and covers the various aspects of creating and maintaining an effective Cyber Security Management System (CSMS).
- IEC 62443 3-X: System: This category focuses on the technical requirements for the development of systems and its primary target group is ‘Solution Providers’.
- IEC 62443 4-X: Component: This last category contains technical guidelines for the development of IACS components by, for example, ‘Manufacturers’. In addition, this category of standards can help ‘System Integrators’ and ‘End Users’ in purchasing secure components for use in their systems.
The figure below shows the layout of the IEC 62443 series of standards graphically.
Eye of the needle?
Cyber-attacks on critical infrastructure can have far-reaching consequences and disrupt society. After all, electricity plants, pumping stations, hospitals, food factories, energy suppliers, etc. are increasingly dependent on OT systems. It is of particular importance that these OT systems are properly secured, including protection against cyber-attacks. In the case of the Florida water recycling facility, there luckily were no casualties. Perhaps the water company's customers have threaded the eye of the needle. What if it had gone wrong? Is the cyber security of your OT system well organized?
More info?
Assessments according to the IEC 62443 series of standards require specialist knowledge, especially in the field of cybersecurity and OT systems. Kiwa's security experts have this knowledge. Would you like to know more about cybersecurity and OT systems? Contact us via e-mail (cybersecurity@kiwa.com) or phone (+31 (0)88 998 49 00)


